INTRODUCING FPI SOC
THE FUTURE OF SECURITY OPERATIONS
At FPI Security Services we are proud to unveil FPI SOC – our state-of-the-art Security Operations Center. Equipped with cutting-edge technology and staffed by highly trained security professionals. FPI SOC sets a new standard in proactive threat detection and incident response.
Whether monitoring live video feeds, managing emergency situations or coordinating field personnel, FPI SOC is dedicated to ensuring the safety and security of our clients around the clock. Discover how FPI SOC can provide unparalleled protection and peace of mind for your business. Our center provides 24×7 monitoring, detection, and response, ongoing risk management, as well as security awareness training to proactively protect your business while continually strengthening your security posture.
Security Operations Center Services
Our technologically advanced security solutions are aimed at providing peace of mind, utilizing Artificial Intelligence (AI) to assist clients with their day-to-day needs. Here are the features that our solutions provide to benefit the needs of customers:


1. VIDEO ANAYLTICS
Our team is able to leverage artificial intelligence (AI) and machine learning (ML) to analyze video feeds in real-time to identify and assess potential security threats. These systems are capable of detecting suspicious activities such as unauthorized access, loitering, and unusual movement patterns, which may indicate a security breach or other threat. With threat detection protocols SOC operators focus on critical incidents by filtering out non-threatening activities and highlighting anomalies that require immediate attention.
This proactive approach enables quicker and more accurate responses to potential threats, reducing the likelihood of incidents escalating into serious security breaches. For example, video analytics can alert security personnel to individuals displaying unusual behavior, such as loitering near sensitive areas, enabling preemptive intervention. Additionally, video analytics supports the coordination of incident responses by correlating data from multiple security systems, such as access control and alarm systems. This comprehensive analysis provides a more complete understanding of potential threats, facilitating better decision-making and ensuring a swift and effective response.
Key Features and Benefits of Video Analytics
- Real-Time Threat Detection and Analysis
- Integration with Other Security Systems
- Proactive Response Protocols
- Improved Incident Response Coordination
- Operational Insights and Efficiency
The integration of video analytics with threat detection protocols enables SOC operators to focus on critical incidents by filtering out non-threatening activities. This technology is capable of identifying subtle indicators of potential threats, such as unusual behavior patterns or repeated access attempts in sensitive areas. It is can also identify patterns and trends, such as peak traffic times or frequently accessed areas, which can inform operational improvements and resource allocation. These insights help clients optimize their operations while ensuring their properties and assets remain secure.
2. REMOTE VIDEO MONITORING
Remote agent monitoring is a transformative approach to modern security management, enabling security personnel to oversee multiple sites from a centralized location. This method leverages advanced video surveillance, sensor technology, and communication tools to provide comprehensive oversight and ensure the safety and security of various properties. By centralizing these functions within a Security Operations Center (SOC), organizations can enhance their security capabilities while achieving significant cost savings and operational efficiencies.

Key Features and Benefits of Remote Video Monitoring
- Centralized Surveillance
- Real-Time Monitoring and Response
- Scalable Solutions and Cost Savings
- Enhanced Operational Efficiency
By integrating video monitoring systems from multiple locations into a Security Operations Center, this centralized approach ensures continuous surveillance and quick identification of potential security threats. Remote monitoring systems are equipped with advanced sensors and real-time communication tools that allow agents to quickly respond to incidents. Whether it’s detecting unauthorized access, monitoring environmental conditions, or managing alarms, these systems provide immediate feedback and allow for swift action coupled with 24/7 oversight.
3. AUTONOMOUS RESPONSE
Autonomous response systems leverage artificial intelligence and machine learning to automate security protocols based on situational factors and programming. These systems can independently detect, assess, respond to threats, and therefore reduce the need for human intervention. This eliminates the need for security guards to be in any potential harms’ way.

Key Features and Benefits of Autonomous Response
- Automated Threat Detection and Response
- Reduction in Human Exposure to Danger
- Customizable Responses and Messaging
- Handle Multiple Incidents Simultaneously
- Escalation Management
Autonomous responses provide a robust security solution that operates 24/7, ensuring continuous protection and peace of mind for clients. When a potential threat is detected, the system can autonomously decide on the best course of action, whether that means sounding an alarm, locking down a facility, sending alerts to security operators or dispatching local law enforcement. This capability ensures that threats are addressed promptly, minimizing the risk of harm and damage to property or personnel. By automating responses to potential threats, these systems eliminate the need for direct human involvement in potentially hazardous scenarios. This flexibility ensures that the system operates in alignment with the client’s security strategy and business requirements.
4. LOITERING DETERRENT
This system uses sophisticated algorithms to analyze video feeds in real-time, detecting patterns of behavior that may indicate loitering or other suspicious activities. By identifying and addressing individuals, the analytics can differentiate between normal and unusual behavior, ensuring that alerts are triggered only when necessary. These automated responses can be: activating alarms, deploying talk down audio to ask the individual(s) to leave the area before the situation escalates, or contacting local law enforcement. The loitering deterrent system helps reduce the risk of vandalism, theft, and unauthorized access, in order to give clients peace of mind.

Key Features and Benefits of Loitering Deterrent Systems
- Advanced Video Analytics and Automated Responses
- Enhanced Site Security
- Prevention of Criminal Activity
- Integration with Existing Security Systems
Loitering deterrence systems can be seamlessly integrated with other security measures, such as access control systems, surveillance cameras, and lighting controls. This integration allows for a coordinated response to detected threats, enhancing the effectiveness of the overall security strategy. Loitering deterrence systems contribute to maintaining a secure environment by ensuring that only authorized individuals are present in sensitive areas. This is particularly important in locations such as financial institutions, government buildings, and high-security facilities where unauthorized presence can lead to significant risks.
5. TALK DOWN AUDIO
Talk down audio systems are a powerful tool in security management, enabling remote operators to communicate directly with intruders or suspicious individuals in different locations. These systems utilize strategically placed loudspeakers to deliver clear, authoritative messages, which can deter unwanted behavior and de-escalate potentially dangerous situations. The ability to intervene in real-time without requiring a physical presence on the scene significantly enhances both the safety and efficiency of security operations.
The primary benefit is the ability to intervene in real-time without physical presence, enhancing safety for security personnel. Talk down audio systems also serve as a psychological deterrent, as the awareness of being monitored and addressed can discourage criminal activity. Clients benefit from increased control and the ability to prevent incidents proactively. This can also be escalated if the situation arises, and local law enforcement can be dispatched as well to keep client’s businesses safe and secure.
Key Features and Benefits of Talk Down Audio
- Real-Time Communication and Intervention

- Strong Psychological Deterrence
- Integration with Other Security Systems
- Enhanced Safety for Security Personnel
- Proactive Incident Prevention
- Escalation Management
The ability to communicate directly with potential intruders or individuals in restricted areas allows operators to issue warnings, instruct them to leave the premises, or provide information that could prevent the situation from escalating. This real-time response is crucial in preventing criminal activity and maintaining order. One of the most powerful aspects of talk down audio systems is notifying any suspicious individuals that they are being monitored. The clear, authoritative nature of the messages delivered through these systems reinforces the presence of an active security force, which can be enough to discourage further action.
6. VIRTUAL GUARDING
Incorporating virtual guarding services into a security plan allows FPI's SOC personnel to communicate with individuals on-site in real-time, regardless of the situation. This real-time dialogue enhances response times, improves coordination during emergencies, and boosts overall situational awareness. By utilizing mobile devices, intercoms, radios, and more, virtual guarding ensures seamless communication, making security operations more responsive and effective. For clients, this means minimized risks and a safer environment for everyone involved.
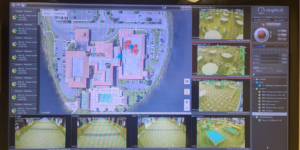
Key Features and Benefits of Virtual Guarding
- Real-Time Interaction
- Versatile Communication Tools
- Enhanced Coordination and Command
- Quicker Incident Resolution
The versatility of virtual guarding systems ensures uninterrupted communication, even in challenging environments or over large distances. These systems enable SOC personnel to receive real-time updates from the field, providing a clearer and more accurate understanding of the situation. Whether dealing with a minor security issue or a major emergency, the prompt exchange of information allows for more efficient problem-solving, minimizing the potential impact on the client's operations and ensuring a safer environment for everyone involved.
7. LICENSE PLATE RECOGNITION (LPR)
License Plate Recognition (LPR) systems use cameras and software to capture and analyze license plate information. These advanced cameras can automatically collect license plate information, identify stolen or unauthorized vehicles, and integrate with other security systems for a robust solution for clients in order for them to know who is coming in and out of their properties or sites.
Key Features and Benefits of Two Way Communication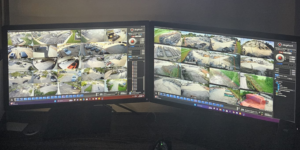
- Automated Vehicle Logging and Monitoring
- Identification of Stolen or Unauthorized Vehicles
- Improved Traffic Control and Access Management
- Valuable Data Collection for Investigations
One of the primary security benefits of LPR systems is their ability to cross-reference captured license plates with databases of stolen or unauthorized vehicles. This capability allows for real-time identification of potential security threats, enabling swift action to prevent unauthorized access or apprehend individuals involved in criminal activities. When integrated with other security measures, such as barrier controls or alarms, LPR systems can automatically trigger alerts or lockdowns if a suspicious vehicle is detected.
